Using OPNsense and IP blocklists to block malicious traffic
Blocking traffic from malicious IPs with OPNsense using public IP blocklists is simple and effective. Read how it's done:

Photo by Kai Pilger on Unsplash
Why Blocking on Layer 3/4 is effective and efficient
Blocking malicious IPs is simple and effective. On one hand it prevents connections to known bad actors from the beginning and on the other hand, should a client become compromised, communication will be blocked reliably before things may escalate further. Of course this only works as good as the content of the used blocklists is.
While blocking on IP level may seem like a "brute force" approach it is in fact very simple, effective and reliable, it intercepts connections already at Layer 3/4 of the OSI model. Since this happens very early and already on a low level of the networking stack, the costs in terms of performance are almost nothing compared to more sophisticated approaches doing comparable on Layer 7.
Blocking IPs with blocklists on Layer 3/4 is:
- Effective
- Reliable
- Simple to set up and maintain
- Comes at almost no performance cost
Certainly there are alternative approaches to achieve comparable results. However nothing beats blocking at Layer 3/4 if one wants to prevent connectivity to a specific IP completely. That said it absolutely makes sense to have complementary measures on other Layers such as DNS blocklists and deep packet inspection in place, also to catch things that might slip through the coarse grained IP Level blocking only.
External blocklists with OPNsense
The use and the management of externally provided IP blocklists with OPNsense is very simple and efficient, aliases are the tool of choice for this.
Step 1 - Creating an alias for an external blocklist
OPNsense supports the use of externals blocklist within aliases and aliases can be used for firewall rules. The start is therefore to create an alias for the desired blocklist and selecting the URL Table (IPs) type.
I chose to use a distinct alias for every blocklist type in order to be able to configure the update interval individually and be able to activate/deactivate each one independently. For the update interval make sure to respect the recommendations from the list provider to not create unnecessary load on their infrastructure.
Hint: Use a capital letter alias prefix in order for your custom aliases to appear before the system created ones to find them on top of the list.
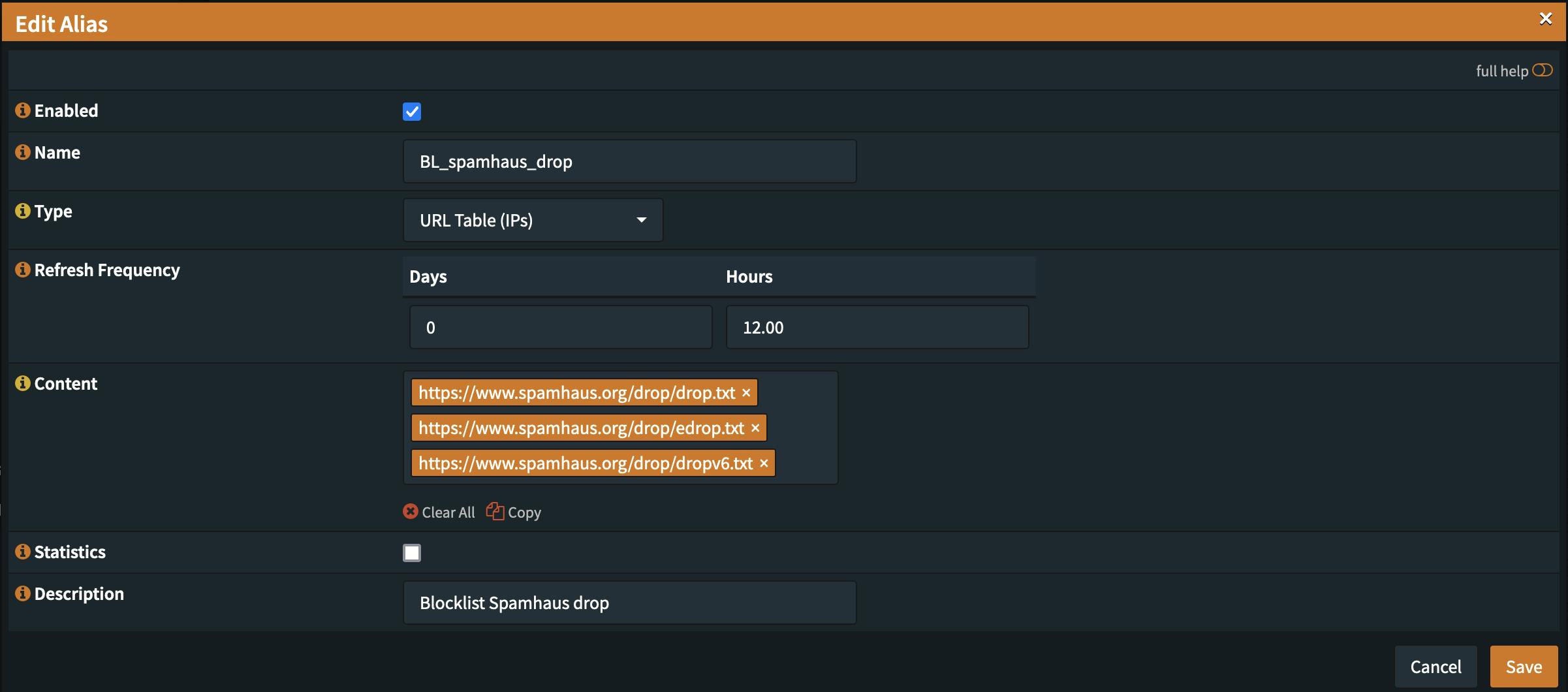
For this example spamhaus drop and edrop was used with an update frequency of 12 hours.
https://www.spamhaus.org/drop/drop.txt
https://www.spamhaus.org/drop/edrop.txt
https://www.spamhaus.org/drop/dropv6.txt
Always inspect the content of the lists prior to first use in order to avoid any unpleasant surprises. Some lists contain private IPs that may result in blocking local traffic and may even ultimately lock you out of your firewall if you're not careful.
Step 2 - Configuring a firewall rule
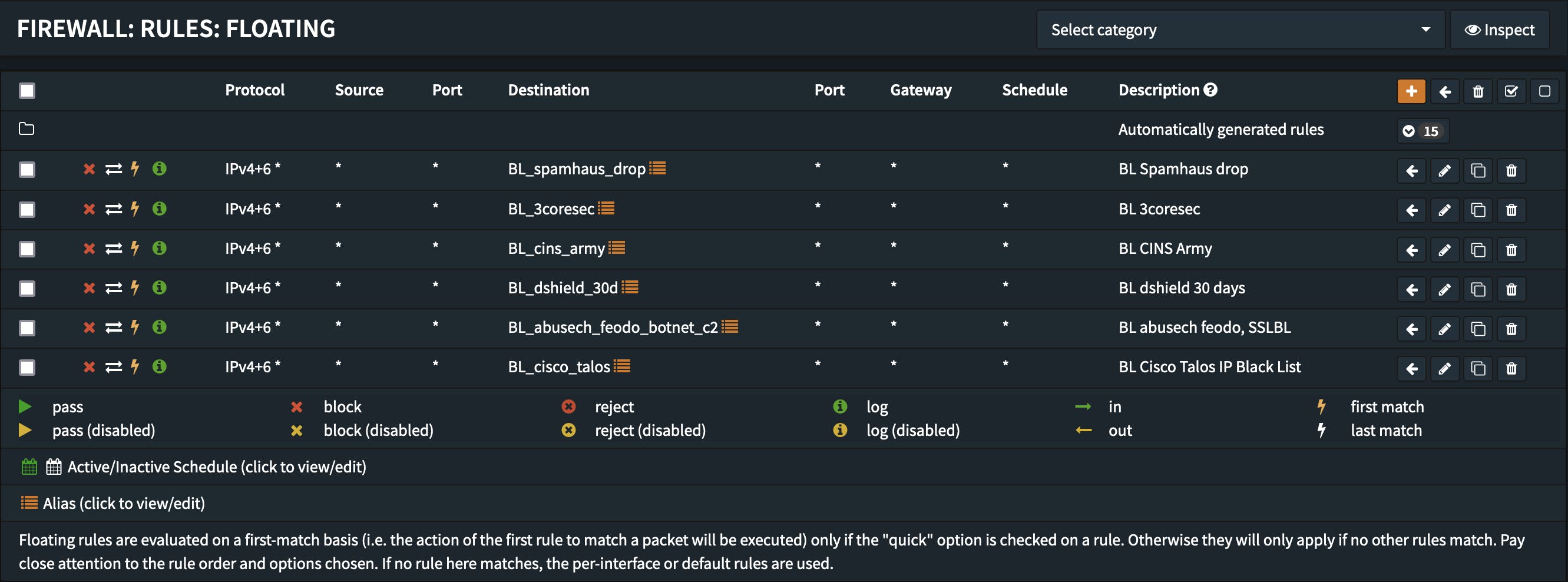
This is one of the situations where it can make sense to configure a floating rule since you want to block traffic to and from any of these IPs independent of the interface or direction it is originating from at the earliest possible occasion.
That said just a WAN rule would also be sufficient to block traffic from and to the WAN interface(s).
Note: Using the floating type rule requires you to be extra careful with the content of the blocklists as you might lock yourself out if the list contains private IP address ranges. OPNsense should theoritically prevent you from locking yourself out with standard settings but you may not want to test it.
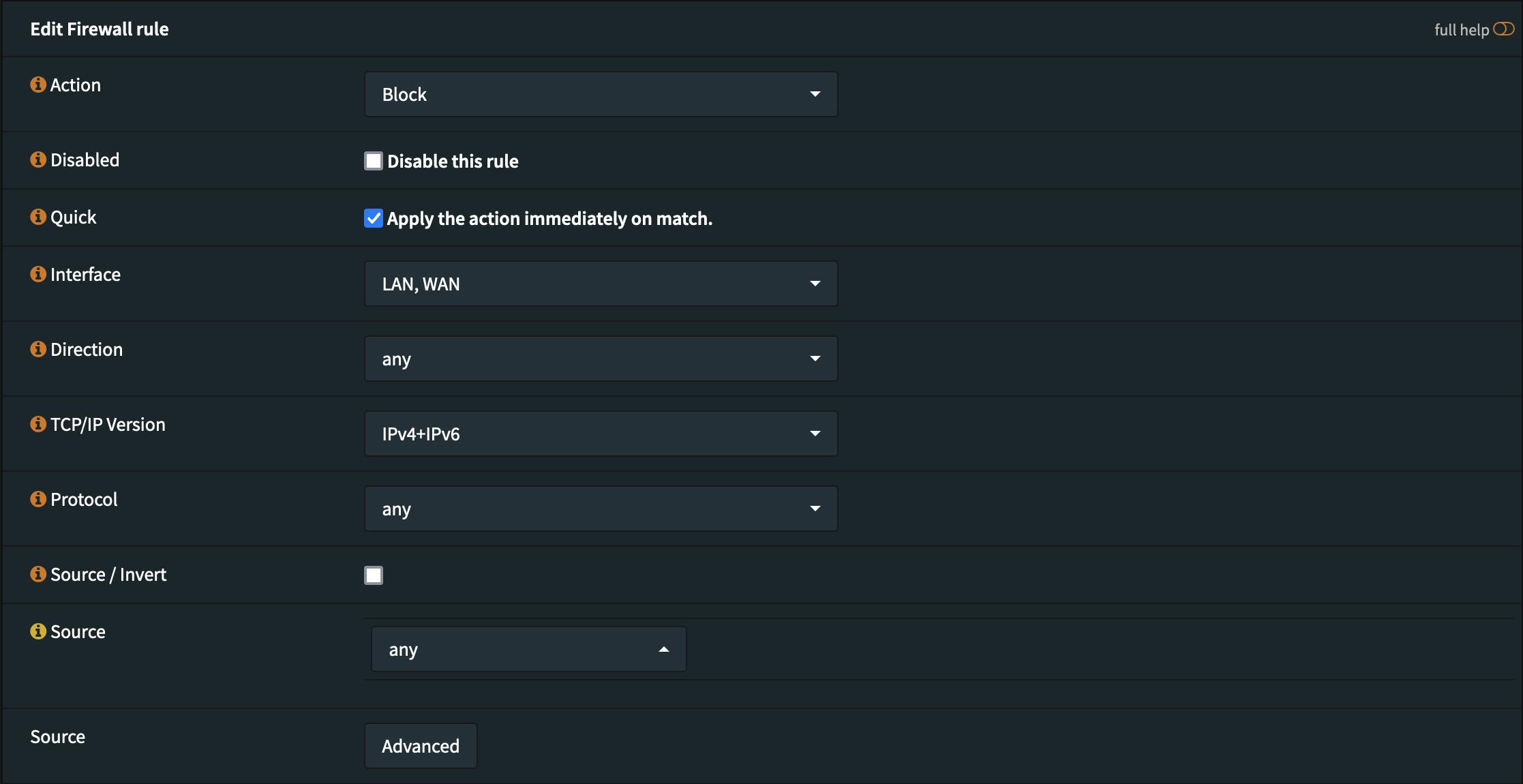
Rule category: Floating
Action: Block
Direction: Any
TCP Version: IPv4+IPv6
Protocol: any
Logging: Active
Make sure you that you choose the correct settings for Direction, TCP Version, Protocol to make the rule applying to all traffic, directions, TCP Versions and Protocols.
Activating logging is also recommended in addition to a meaningful description of your rule to be able to easily consult the log and understand what is happening at any time. Especially after a few you months you may no remember everything so well anymore without a clear description.
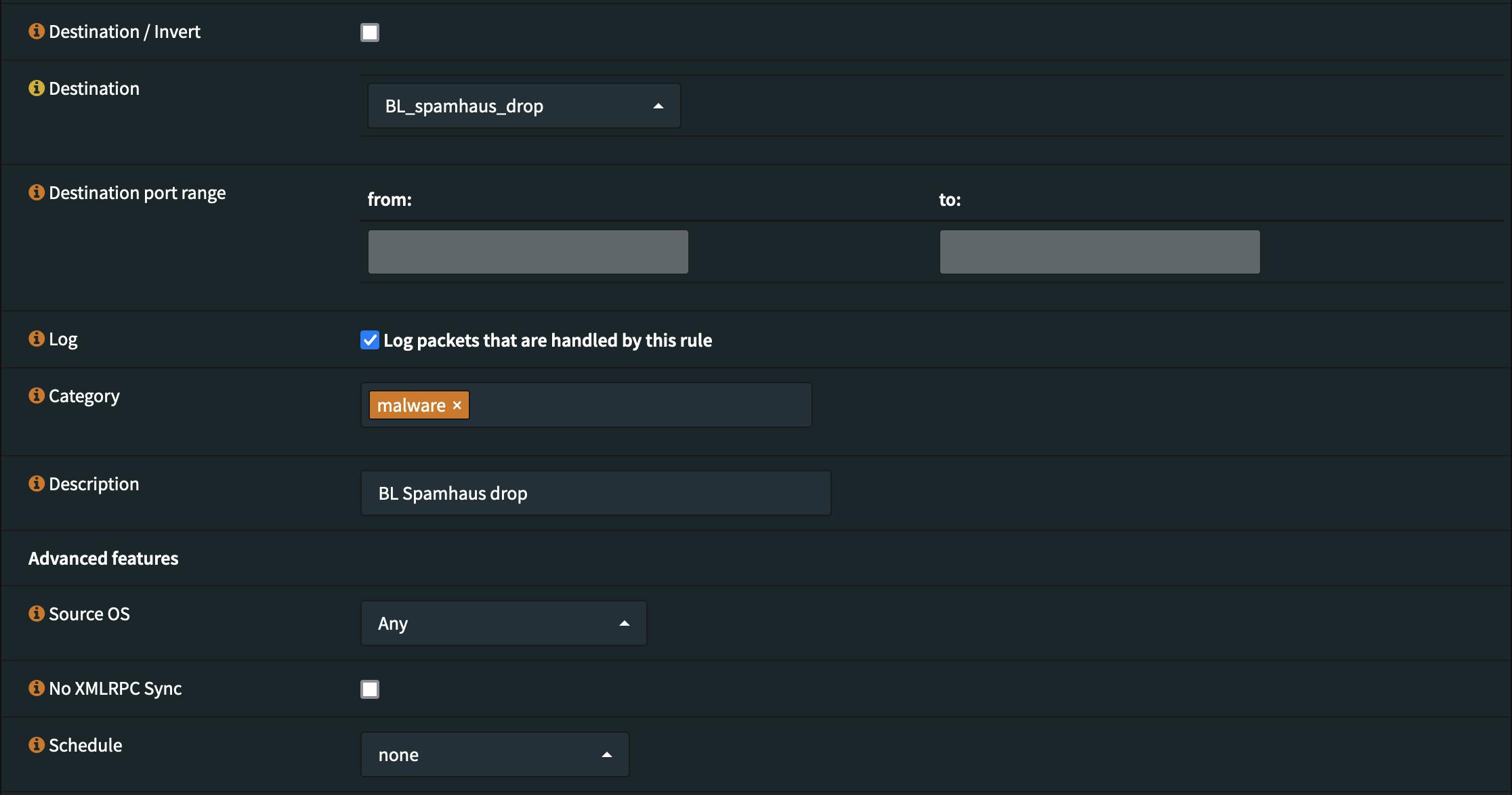
Now save the rule and click the Apply changes button in order for the rule to become active.
Step 3 - Verification of the new firewall rule
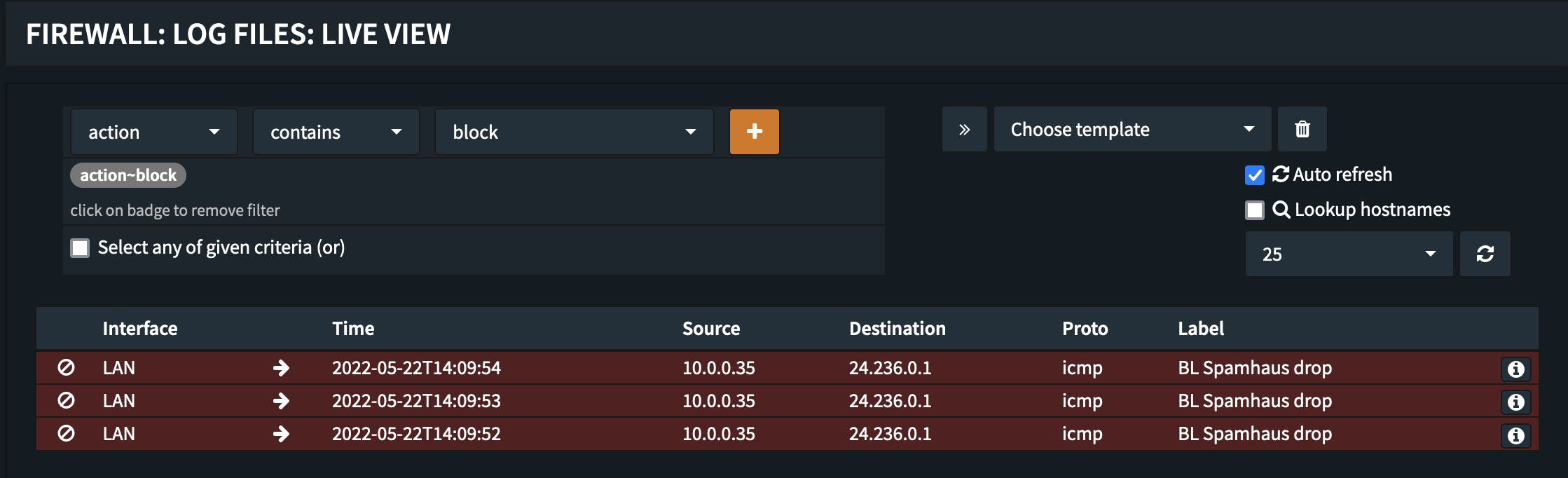
For the next minutes/hours you want to keep an eye on the log to be sure everything works as desired. We nevertheless want to quickly verify that the new rule works as desired. We therefore pick an IP from one of the blocklists and try to connect.
ping -c 3 24.236.0.1
PING 24.236.0.1 (24.236.0.1) 56(84) bytes of data. --- 24.236.0.1 ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 2050ms
As expected pinging or trying to connect to a in the blocklist contained IP does not work and it is also observable in the firewall live log that the traffic is being blocked.
What next
Now with the foundational mechanism explained and the basic setup working this can easily be extended to additional blocklists for blockling malicious traffic reliably on Layer 3/4.
Note: If you use this feature extensively it may be necessary to increase the Firewall Maximum Table Entries or other values in "Settings -> Advanced" in the firewall section.
Complementary to this basic level of protection it is of course always recommended to use additional layers of protection such as DNS filtering or Layer 7 firewall capabilities. OPNsense offers both as well.
Stay safe and secure.
Addendum - Blocklist URLs
The URLs of the blocklists used above are:
# BL_3coresec
https://blacklist.3coresec.net/lists/all.txt
# BL_abusech_feodo_botnet_c2
https://sslbl.abuse.ch/blacklist/sslipblacklist.txt
https://feodotracker.abuse.ch/downloads/ipblocklist_recommended.txt
# BL_cins_army
https://cinsscore.com/list/ci-badguys.txt
# BL_cisco_talos
https://talosintelligence.com/documents/ip-blacklist
# BL_dshield_30d
https://iplists.firehol.org/files/dshield_30d.netset
# BL_spamhaus_drop
https://www.spamhaus.org/drop/drop.txt
https://www.spamhaus.org/drop/edrop.txt
https://www.spamhaus.org/drop/dropv6.txt